Which of the Following Is a Concern About EC Encryption? Solved which of the following best describes the role
If you are looking for Solved 2.1 Explain to a user what encryption is, the benefit | Chegg.com you've visit to the right place. We have 25 Pictures about Solved 2.1 Explain to a user what encryption is, the benefit | Chegg.com like Encryption at Vani, Reduce your Cyber Risk with High-Speed Encryption - DornerWorks and also Several Drawbacks Of Deniable Encryption Technology Encryption For Data. Here it is:
Solved 2.1 Explain To A User What Encryption Is, The Benefit | Chegg.com
 www.chegg.com
www.chegg.com
Solved Which Of The Following Enhances (increases) the | Chegg.com
 www.chegg.com
www.chegg.com
Encryption At Vani
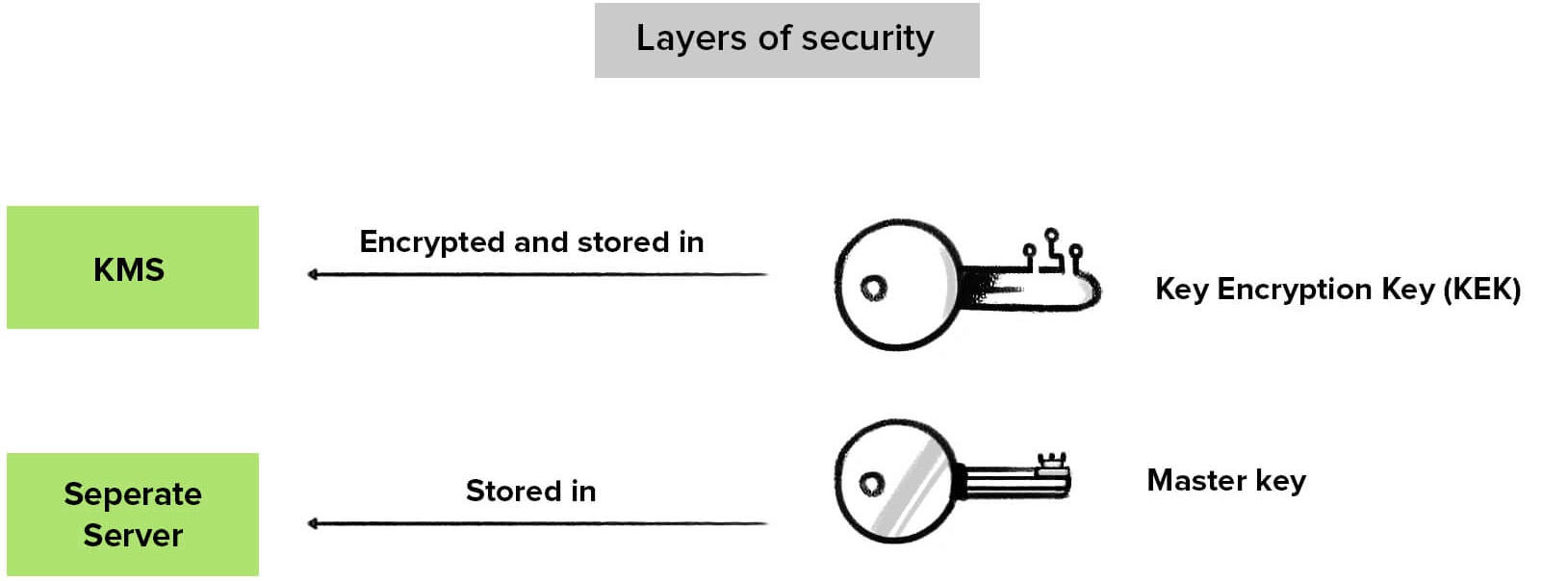 www.vanihq.com
www.vanihq.com
Ethical Considerations Of Encryption | By Cypherdog Security Inc. | May
 medium.com
medium.com
Encryption In Networking
 findnerd.com
findnerd.com
encryption networking secret key
What Is Data Encryption And How Does It Work?
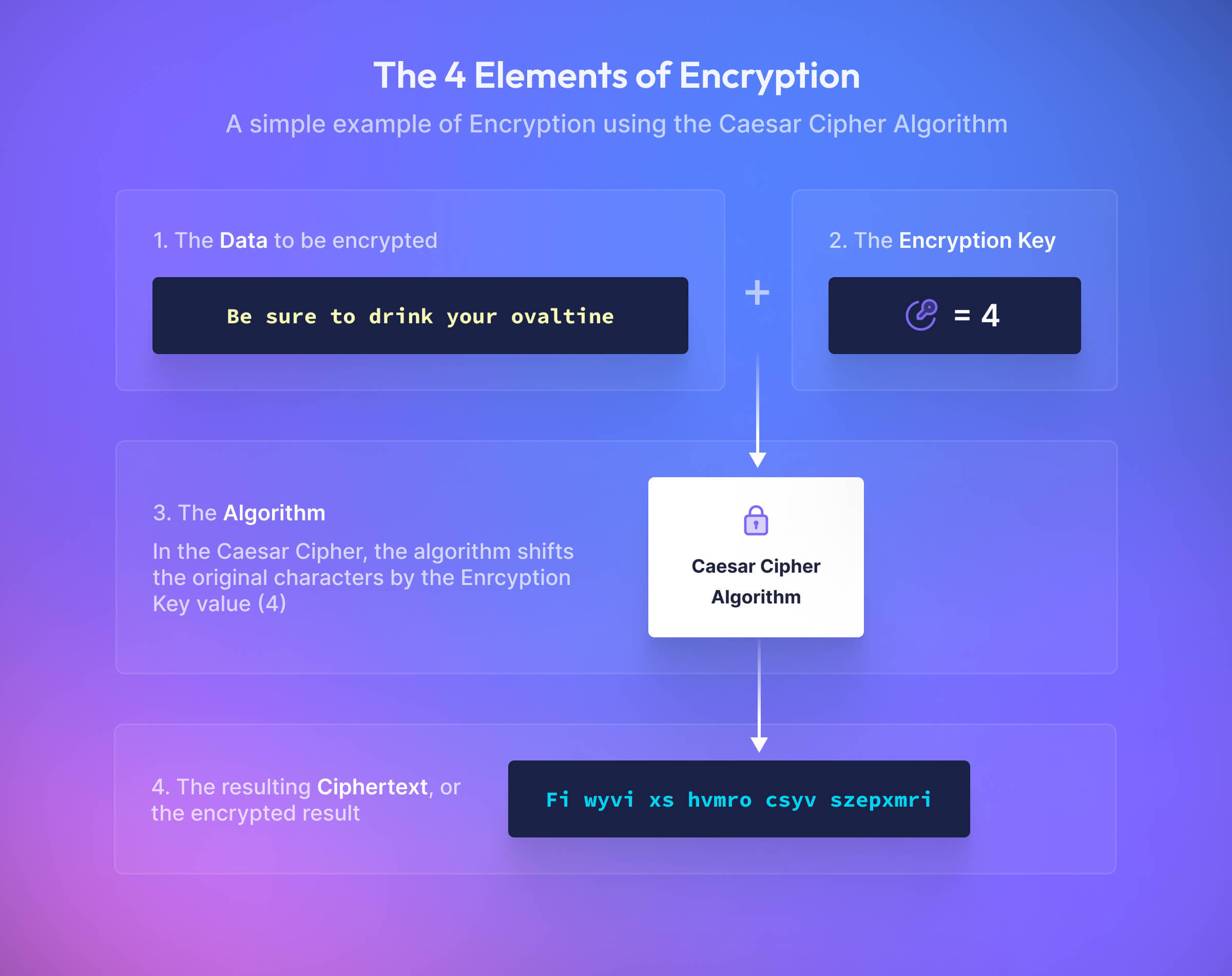 blog.basistheory.com
blog.basistheory.com
Rules Against Weakened Encryption | Information Security Buzz
 www.informationsecuritybuzz.com
www.informationsecuritybuzz.com
encryption trapdoor debate wsj stopping terrorists backdoor
Solved Problem 2. Committing Encryption. A Common Mistake | Chegg.com
 www.chegg.com
www.chegg.com
Regulated Encryption Isn’t Possible — Here’s What Is – POLITICO
 www.politico.eu
www.politico.eu
Encryption - Protection Data - Cyber Security And Ethics - Каталог
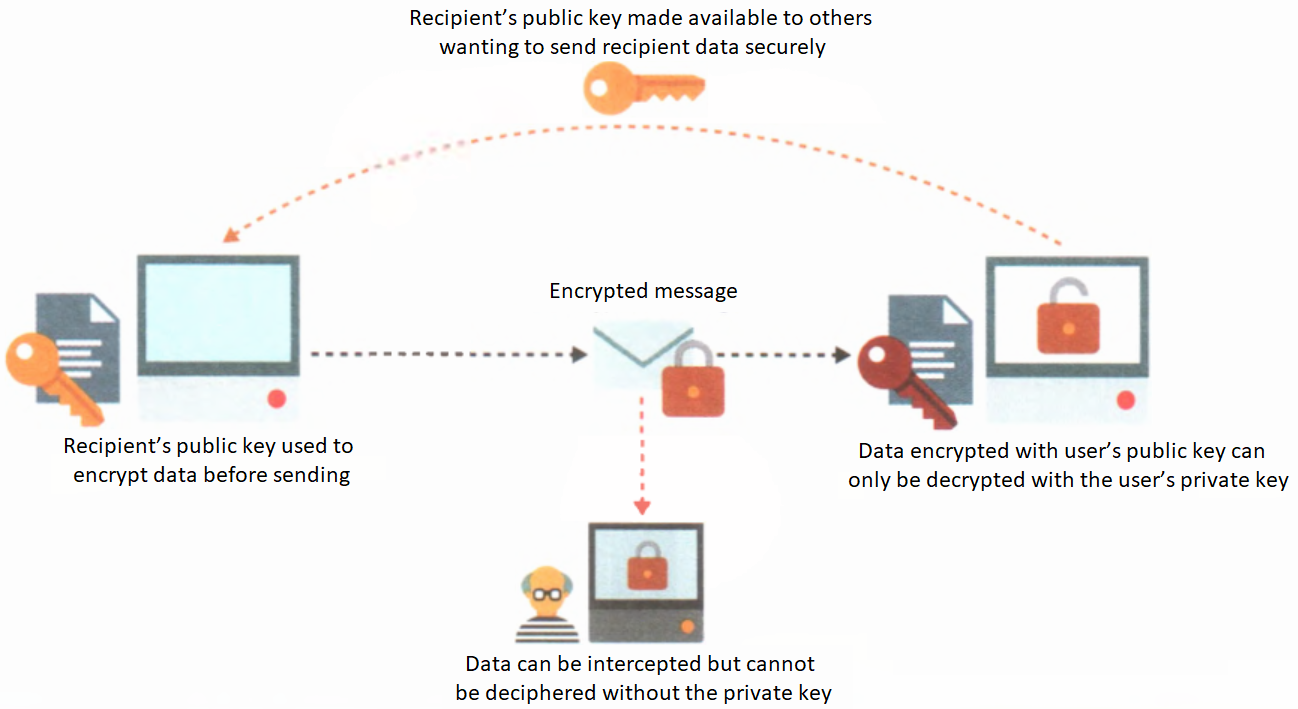 www.bzfar.org
www.bzfar.org
Several Drawbacks Of Deniable Encryption Technology Encryption For Data
 www.slideteam.net
www.slideteam.net
Solved Q 10 Which Of The Following Statements About | Chegg.com
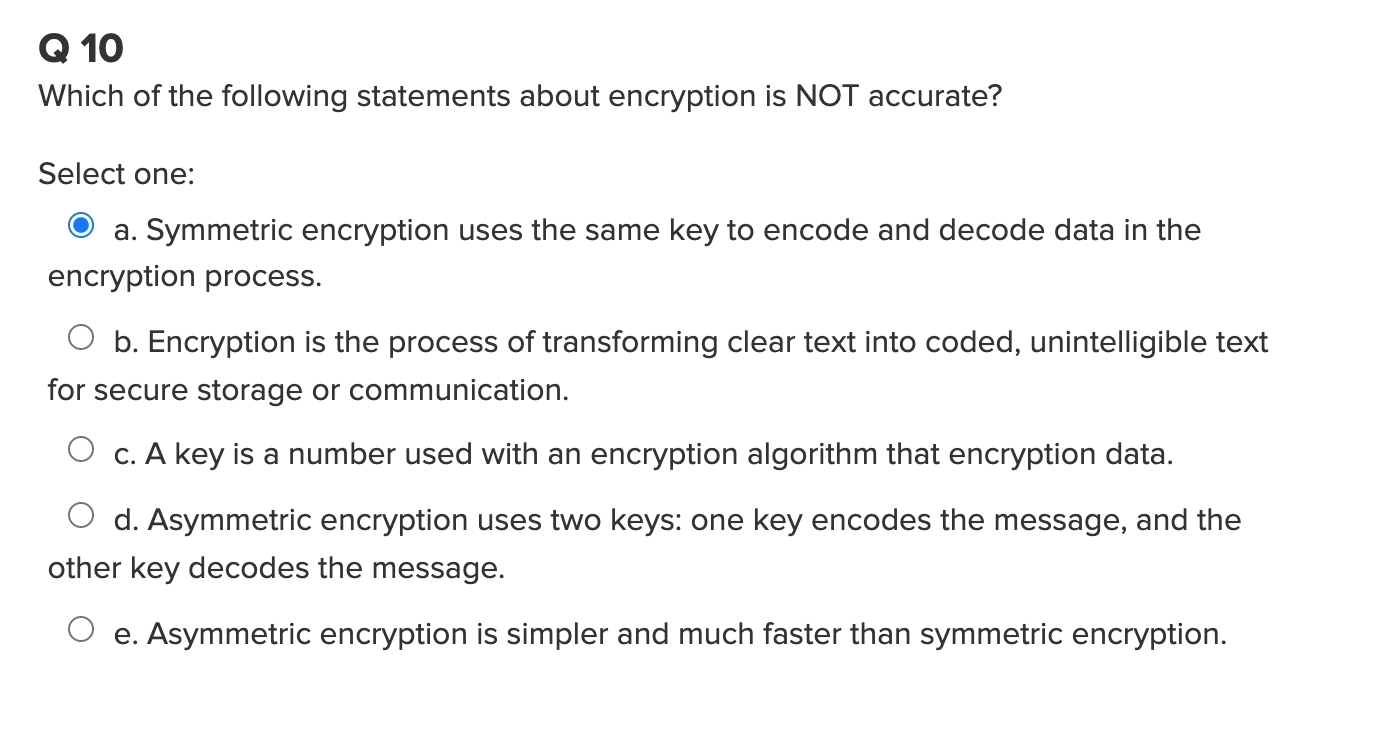 www.chegg.com
www.chegg.com
Encryption | The Key To Compliance And Trust | Snapshot Hub By InterNetX
 snapshot.internetx.com
snapshot.internetx.com
Workshop Exposes Deficiencies Of Electronic Encryption - CNET
 www.cnet.com
www.cnet.com
Who Cares About Encryption? • The Register
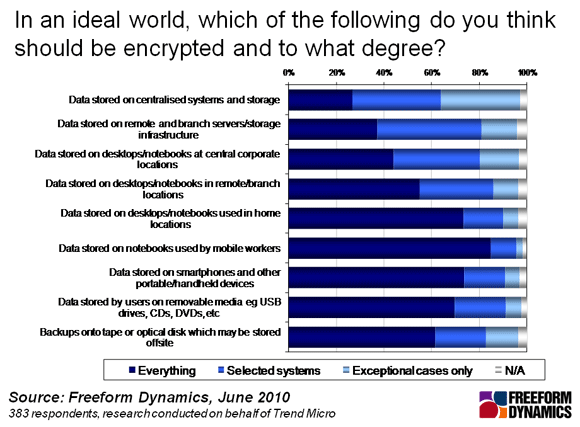 www.theregister.com
www.theregister.com
cares encryption
Solved Which Of The Following Best Describes The Role | Chegg.com
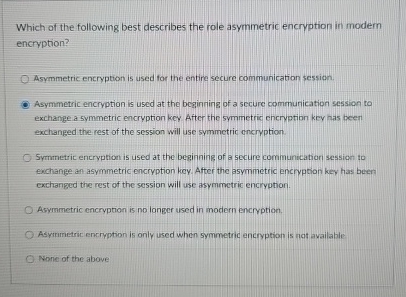 www.chegg.com
www.chegg.com
Solved Which Of The Following Is An Important Security | Chegg.com
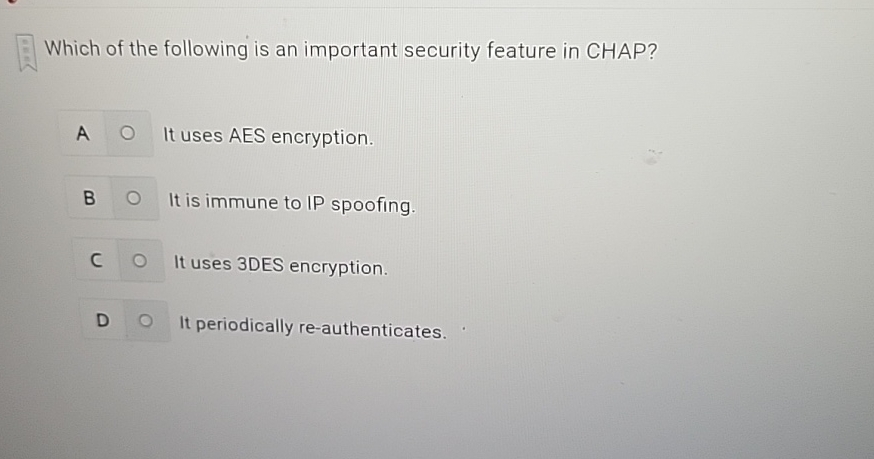 www.chegg.com
www.chegg.com
Solved Question 2 (2 Points) Which Of The Following Is | Chegg.com
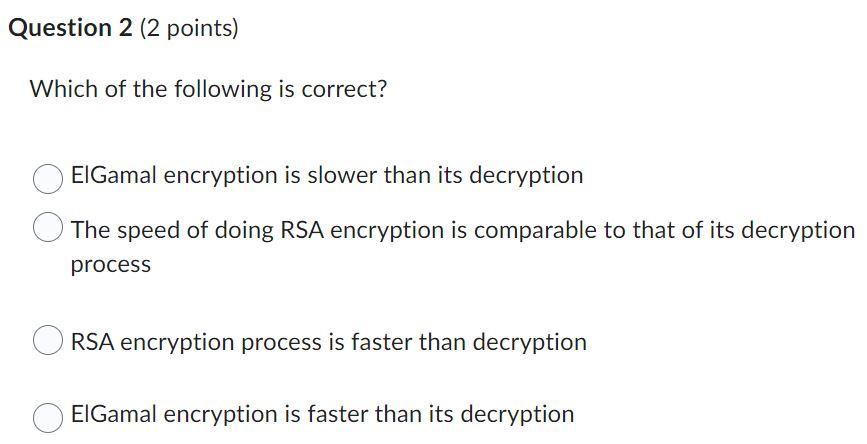 www.chegg.com
www.chegg.com
What Types Of Encryption Are There? | ICO
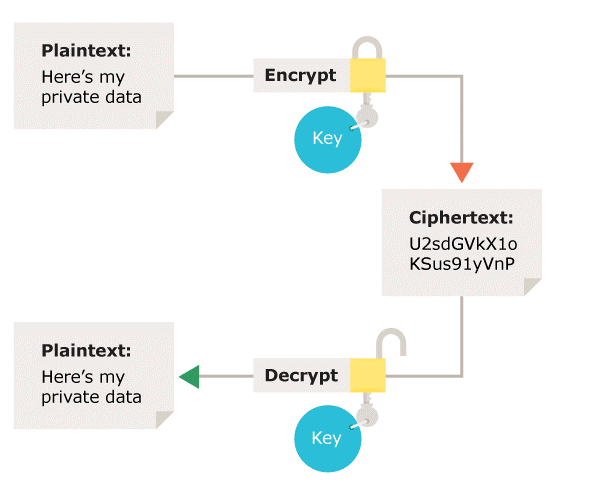 ico.org.uk
ico.org.uk
Can Encryption Algorithms Be Broken – Sekur – Swiss Secure
 sekur.com
sekur.com
Solved Question 46 Of 100 Which Of The Following Encryption | Chegg.com
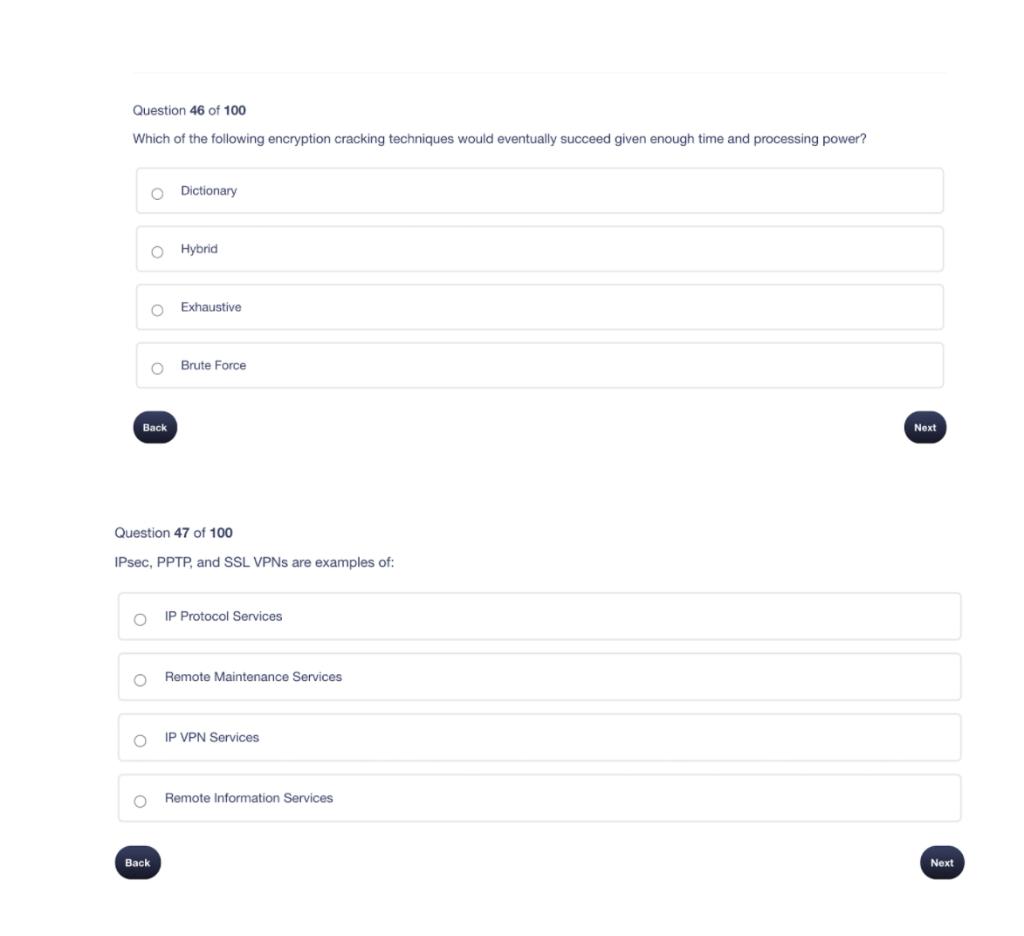 www.chegg.com
www.chegg.com
Solved Which Of The Following Is The Best Description Of | Chegg.com
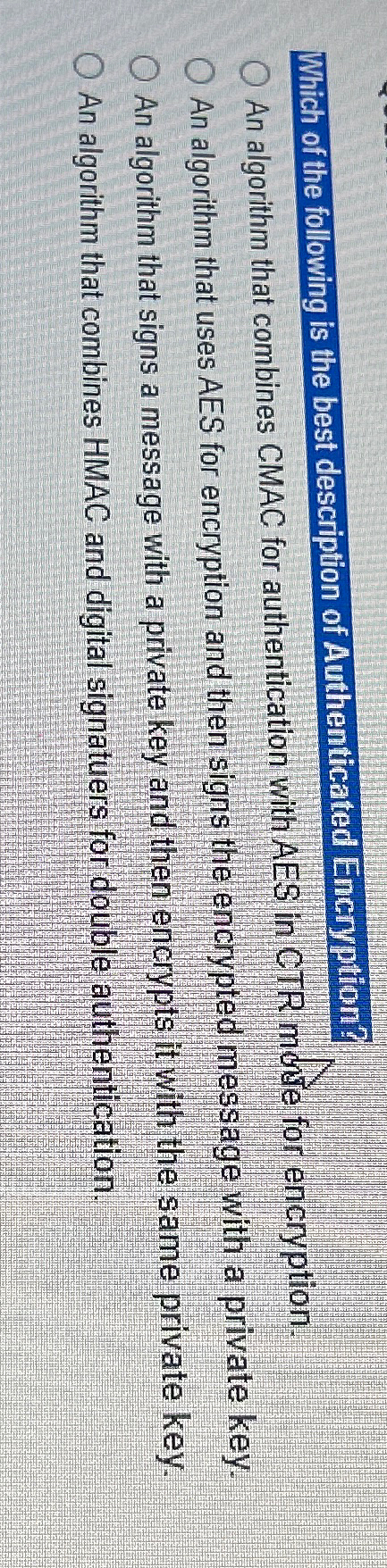 www.chegg.com
www.chegg.com
Reduce Your Cyber Risk With High-Speed Encryption - DornerWorks
 www.dornerworks.com
www.dornerworks.com
Solved Question7 of 8Which Of The Following Is A Secure | Chegg.com
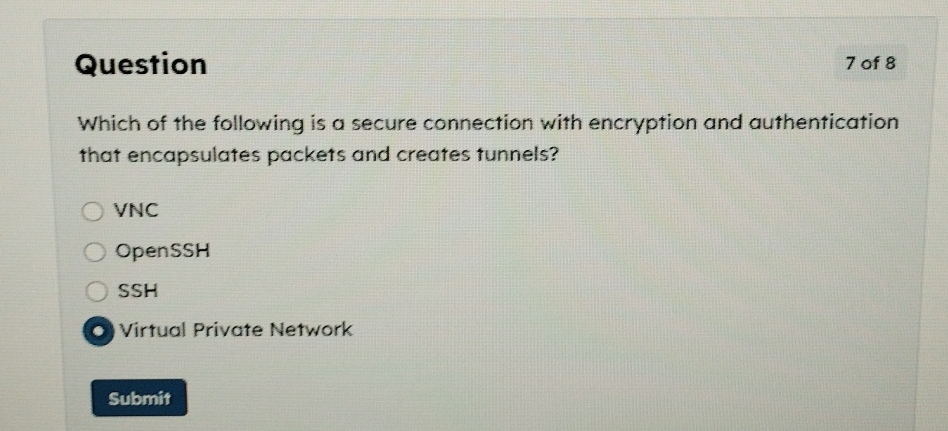 www.chegg.com
www.chegg.com
Solved Problem 4 (20points) The Security Of Encryption Is | Chegg.com
 www.chegg.com
www.chegg.com
Encryption networking secret key. Rules against weakened encryption. What types of encryption are there?