Ensures That the Person Requesting Access: The Key to Cybersecurity A virtual shield with a lock and key symbolizing the secure access to
If you are looking for [Solved] Ensures that the person requesting access to a computer is not you've came to the right page. We have 25 Pictures about [Solved] Ensures that the person requesting access to a computer is not like Solved ensures that the person requesting access to a | Chegg.com, Solved ensures that the person requesting access to a | Chegg.com and also Request Email for Access - Sample Email Requesting Access - Emails In. Read more:
[Solved] Ensures That The Person Requesting Access To A Computer Is Not
![[Solved] Ensures that the person requesting access to a computer is not](https://website-assets.studocu.com/img/document_thumbnails/408f8c2f3c47116e55ff565339bf55ad/thumb_300_388.png) www.studocu.com
www.studocu.com
Fillable Online The Information Requested In This Portion Must Be
 www.pdffiller.com
www.pdffiller.com
PUBLIC ACCESS REQUEST FORM- FWPD - DocumentCloud
 www.documentcloud.org
www.documentcloud.org
Access Letter Sample: Complete With Ease | AirSlate SignNow
 www.signnow.com
www.signnow.com
Request Email For Access - Sample Email Requesting Access - Emails In
 www.emailsinenglish.com
www.emailsinenglish.com
Fillable Online PARTICULARS OF PERSON REQUESTING ACCESS - DV8 Fax
 www.pdffiller.com
www.pdffiller.com
B Particulars Of Person Requesting Access To The Record
 studylib.net
studylib.net
Fillable Online To Be Completed By Person Requesting Access To Or Copy
 www.pdffiller.com
www.pdffiller.com
Intercom Lets Residents, Owners Provide Building Access Via Smartphone
 www.multifamilyexecutive.com
www.multifamilyexecutive.com
building residents smartphone access intercom lets owners provide via able grant guests through their will
Fillable Online SECRETARIAT Library Division Access Request Form For
 www.pdffiller.com
www.pdffiller.com
Hand Giving Icon Vector, Man Person Asking Requesting Help, Taking Or
Six Key Cybersecurity Engineering Activities For Building A
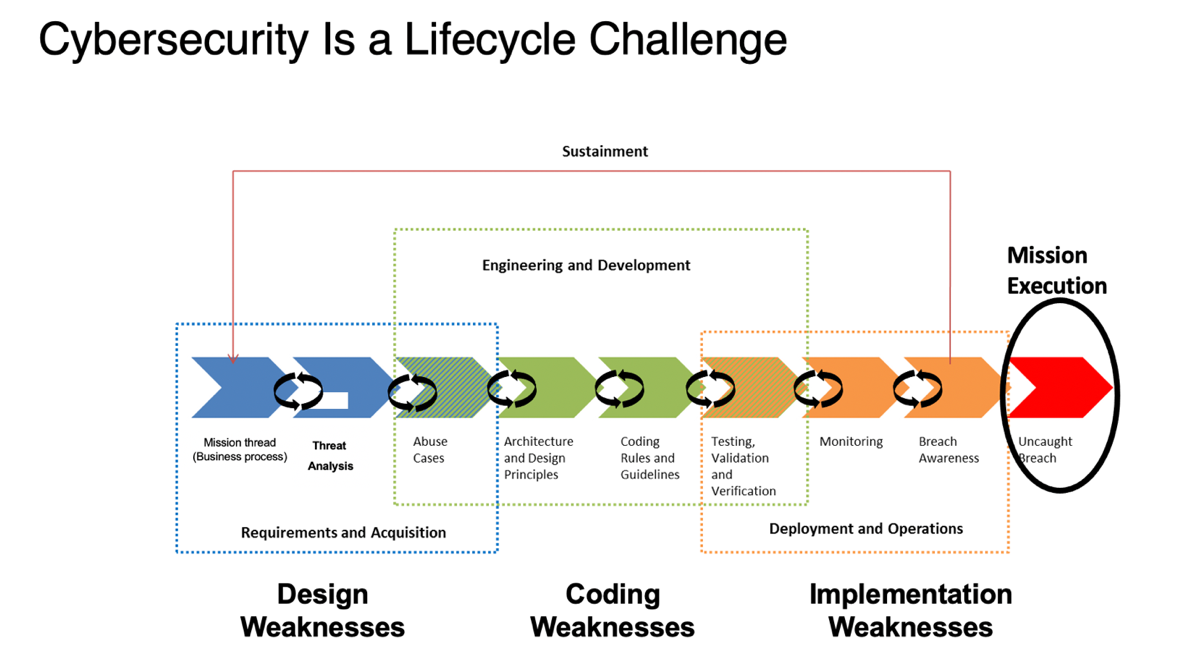 insights.sei.cmu.edu
insights.sei.cmu.edu
cybersecurity lifecycle strategy sei addressing assurance
Unknown Person Requesting Access To File That I Have Never Shared
 support.google.com
support.google.com
file
Fix: "You Don't Have Access" Error On EA App
 bestgamingtips.com
bestgamingtips.com
Network Security Provides Authentication And Access Control For
 storage.googleapis.com
storage.googleapis.com
What Is The Process Of Ensuring That The Person Requesting Access To A
 emcovu.com
emcovu.com
Access To Documents – Representation
 eipamar.com
eipamar.com
Security Personnel Is Opening A Gate With An Automatic System For A
 www.alamy.com
www.alamy.com
[Solved] Ensures That The Person Requesting Access To A Computer Is Not
![[Solved] Ensures that the person requesting access to a computer is not](https://website-assets.studocu.com/img/document_thumbnails/b55c1e55d5ed4e6b7c250b302f1e9722/thumb_300_424.png) www.studocu.com
www.studocu.com
[Solved] Ensures That The Person Requesting Access To A Computer Is Not
A Virtual Shield With A Lock And Key Symbolizing The Secure Access To
 www.dreamstime.com
www.dreamstime.com
Cyber Security And Network Protection With Cybersecurity Expert Working
 www.alamy.com
www.alamy.com
Digital Key, Cybersecurity, Encryption Technology, Safe Access, Virtual
 pixexid.com
pixexid.com
Solved Ensures That The Person Requesting Access To A | Chegg.com
 www.chegg.com
www.chegg.com
Solved Ensures That The Person Requesting Access To A | Chegg.com
 www.chegg.com
www.chegg.com
Fillable online the information requested in this portion must be. Access letter sample: complete with ease. [solved] ensures that the person requesting access to a computer is not